Model Context Protocol (MCP) finally gives AI models a way to access the business data needed to make them really useful at work. CData MCP Servers have the depth and performance to make sure AI has access to all of the answers.
Try them now for free →Access PingOne Data from MySQL in Amazon QuickSight
Connect to PingOne and build visualizations of PingOne data using a MySQL Connection in Amazon QuickSight.
Amazon QuickSight gives you a way to quickly build visualizations, perform analytics, and get insights from AWS data sources, uploaded files, and other databases in the cloud. When paired with the CData SQL Gateway, you get the same functionality with access to 200+ Big Data, NoSQL, and SaaS sources, both on-premises and in the cloud. In this article, we use the SQL Gateway with the CData ODBC Driver for PingOne to access PingOne data through a MySQL connection in Amazon QuickSight, either in real time using direct queries, or by importing the data into SPICE.
Connect to PingOne Data
If you have not already done so, provide values for the required connection properties in the data source name (DSN). You can use the built-in Microsoft ODBC Data Source Administrator to configure the DSN. This is also the last step of the driver installation. See the "Getting Started" chapter in the help documentation for a guide to using the Microsoft ODBC Data Source Administrator to create and configure a DSN.
To connect to PingOne, configure these properties:
- Region: The region where the data for your PingOne organization is being hosted.
- AuthScheme: The type of authentication to use when connecting to PingOne.
- Either WorkerAppEnvironmentId (required when using the default PingOne domain) or AuthorizationServerURL, configured as described below.
Configuring WorkerAppEnvironmentId
WorkerAppEnvironmentId is the ID of the PingOne environment in which your Worker application resides. This parameter is used only when the environment is using the default PingOne domain (auth.pingone). It is configured after you have created the custom OAuth application you will use to authenticate to PingOne, as described in Creating a Custom OAuth Application in the Help documentation.
First, find the value for this property:
- From the home page of your PingOne organization, move to the navigation sidebar and click Environments.
- Find the environment in which you have created your custom OAuth/Worker application (usually Administrators), and click Manage Environment. The environment's home page displays.
- In the environment's home page navigation sidebar, click Applications.
- Find your OAuth or Worker application details in the list.
-
Copy the value in the Environment ID field.
It should look similar to:
WorkerAppEnvironmentId='11e96fc7-aa4d-4a60-8196-9acf91424eca'
Now set WorkerAppEnvironmentId to the value of the Environment ID field.
Configuring AuthorizationServerURL
AuthorizationServerURL is the base URL of the PingOne authorization server for the environment where your application is located. This property is only used when you have set up a custom domain for the environment, as described in the PingOne platform API documentation. See Custom Domains.
Authenticating to PingOne with OAuth
PingOne supports both OAuth and OAuthClient authentication. In addition to performing the configuration steps described above, there are two more steps to complete to support OAuth or OAuthCliet authentication:
- Create and configure a custom OAuth application, as described in Creating a Custom OAuth Application in the Help documentation.
- To ensure that the driver can access the entities in Data Model, confirm that you have configured the correct roles for the admin user/worker application you will be using, as described in Administrator Roles in the Help documentation.
- Set the appropriate properties for the authscheme and authflow of your choice, as described in the following subsections.
OAuth (Authorization Code grant)
Set AuthScheme to OAuth.
Desktop Applications
Get and Refresh the OAuth Access Token
After setting the following, you are ready to connect:
- InitiateOAuth: GETANDREFRESH. To avoid the need to repeat the OAuth exchange and manually setting the OAuthAccessToken each time you connect, use InitiateOAuth.
- OAuthClientId: The Client ID you obtained when you created your custom OAuth application.
- OAuthClientSecret: The Client Secret you obtained when you created your custom OAuth application.
- CallbackURL: The redirect URI you defined when you registered your custom OAuth application. For example: https://localhost:3333
When you connect, the driver opens PingOne's OAuth endpoint in your default browser. Log in and grant permissions to the application. The driver then completes the OAuth process:
- The driver obtains an access token from PingOne and uses it to request data.
- The OAuth values are saved in the location specified in OAuthSettingsLocation, to be persisted across connections.
The driver refreshes the access token automatically when it expires.
For other OAuth methods, including Web Applications, Headless Machines, or Client Credentials Grant, refer to the Help documentation.
When you configure the DSN, you may also want to set the Max Rows connection property. This will limit the number of rows returned, which is especially helpful for improving performance when designing reports and visualizations.
Configure the SQL Gateway
See the SQL Gateway Overview to set up connectivity to PingOne data as a virtual MySQL database. You will configure a MySQL remoting service that listens for MySQL requests from clients. The service can be configured in the SQL Gateway UI.
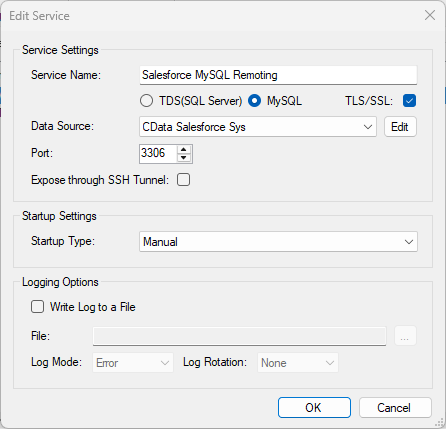
To connect to the SQL Gateway from QuickSight, you will need to run the SQL Gateway on a web-facing machine. After configuring the SQL Gateway, make note of the following information:
- The IP address or domain name of the machine hosting the SQL Gateway
- The data source name (likely CData PingOne Sys) of the MySQL service
- The port number of the MySQL service
- The credentials of a SQL Gateway user with access to the service
Configure Remote Access
If your ODBC Driver and the remoting service are installed on-premise (and not accessible from Amazon QuickSight), you can use the reverse SSH tunneling feature to enable remote access. For detailed instructions, read our Knowledge Base article: SQL Gateway SSH Tunneling Capabilities.
Connect to PingOne in QuickSight
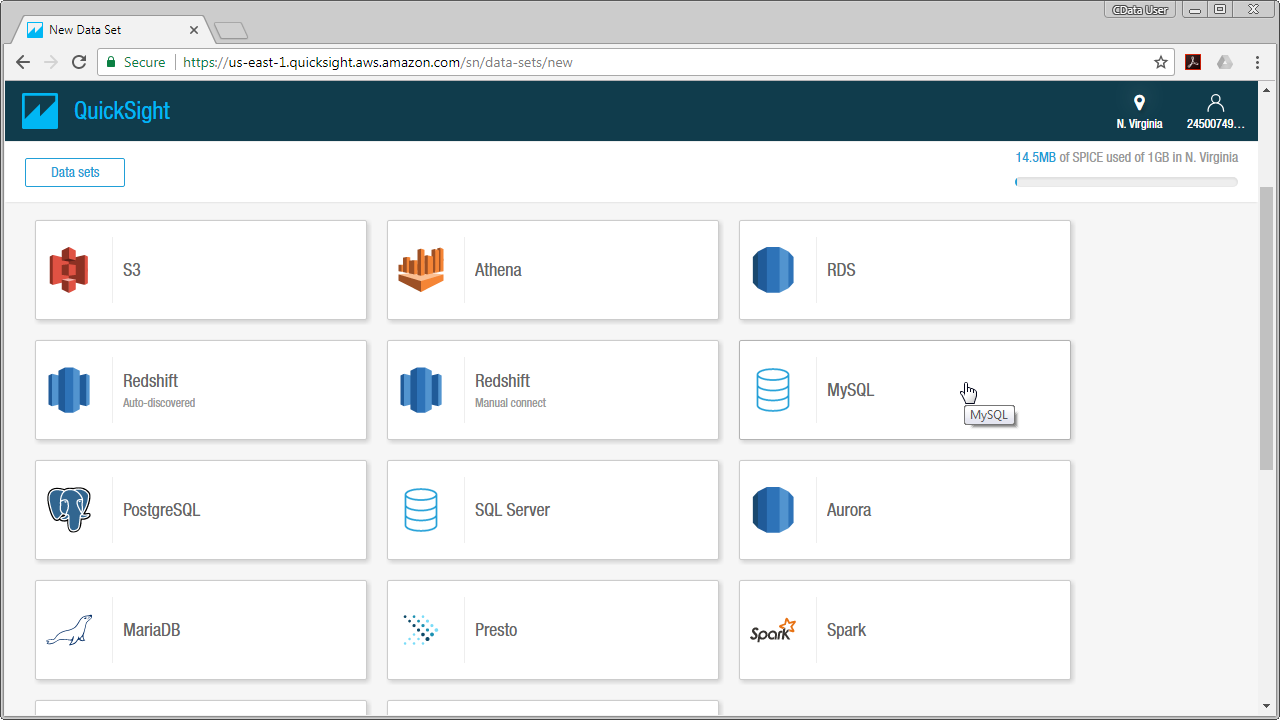
Once you have a MySQL Service configured for the PingOne ODBC Driver, you are ready to connect to the data in QuickSight. Start by logging in to your QuickSight console. From there, click Manage Data, then click New Data Set and choose MySQL as the data source.
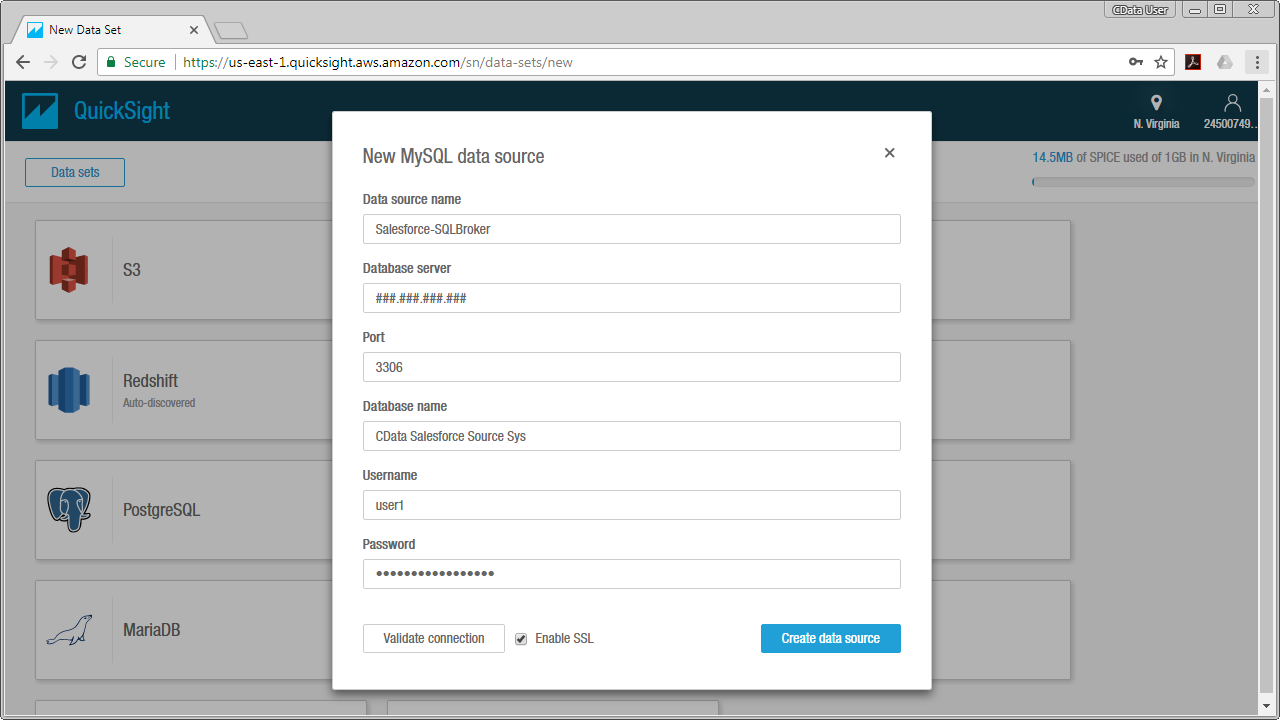
Configure the data set using the values for the MySQL service for PingOne you configured in SQL Gateway (be sure to use the DSN for the database name). Validate your connection and click Create Data Source.
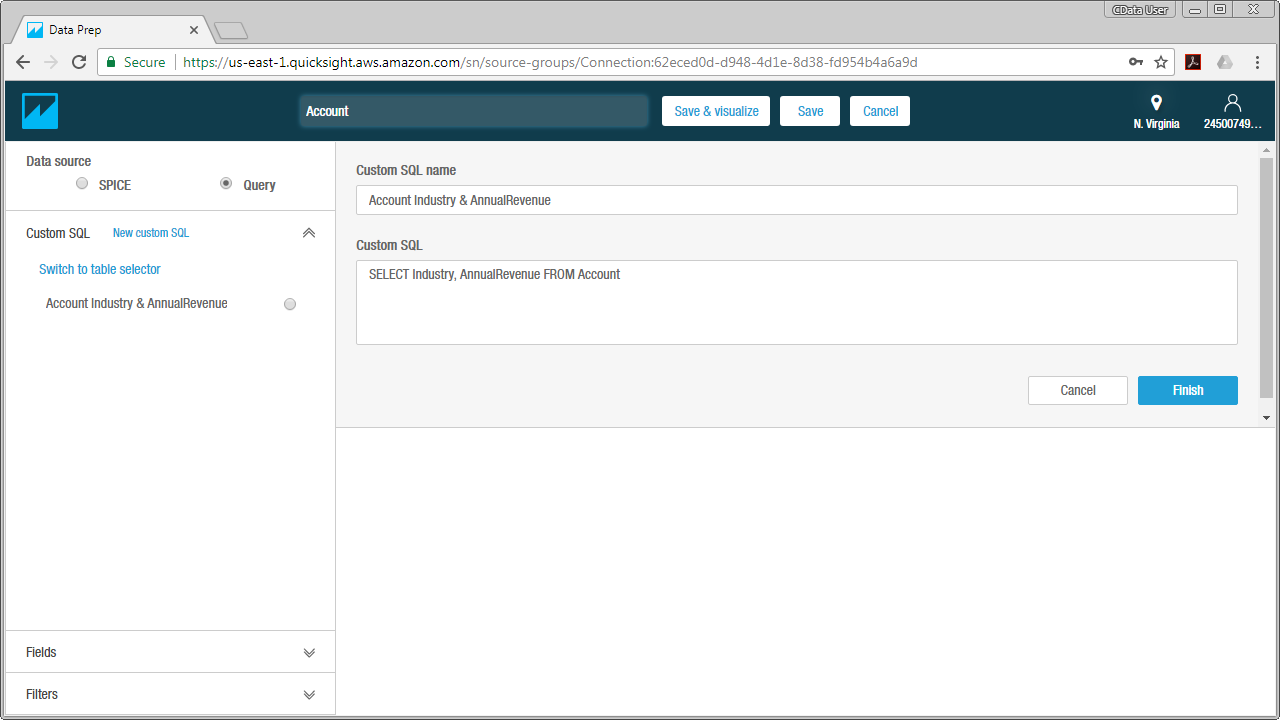
Visualize PingOne Data in QuickSight
For this article, we will use a custom SQL query for our data visualization. To do so, click Edit/Preview Data and in the resulting Data Prep screen follow the steps below:
- Name your data set (for example, [CData].[Administrators].Users).
- If you wish to import your data into QuickSight SPICE, click the SPICE option, otherwise QuickSight will query the data directly.
- Under the Tables menu, click Switch to Custom SQL Tool.
- Give your SQL query a name.
- Enter your custom SQL query. For example:
SELECT Id, Username FROM [CData].[Administrators].Users - Click Finish.
- Click Save & Visualize.
After you have saved the data set, you can configure the visualization. Select the columns you wish to visualize and choose a visual type. Your visualization can be customized, from its name to the way that data is aggregated.
With the CData ODBC Driver for PingOne and SQL Gateway, you are able to easily build data visualizations and perform analytics on PingOne data in Amazon QuickSight. If you have any questions, such as needing to access your on-premises data from AWS QuickSight, let our Support Team know.

